Small tips and useful guides to make life safer on the web and in cyberspace in general but not only.
0
17948
In today's digital landscape, where the collection and use of personal data has become a growing concern for millions of users, Startpage.com emerges ..
0
4083
In the landscape of corporate cybersecurity, the concept of "trust" is undergoing a radical transformation. While until a few years ago the traditiona..
0
4700
The Critical Role of Apache HTTP Server in the Digital LandscapeApache HTTP Server, commonly known as Apache, has maintained a prominent position in t..
0
4371
The Server Message Block (SMB) protocol continues to be a critical infrastructure component in Windows environments, facilitating the sharing of files..
0
3306
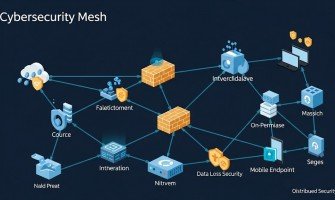
Over
the past decade, the cybersecurity landscape has undergone a radical
transformation, evolving from a set of perimeter defenses to a complex,
i..
0
2906
In the heart of the vibrant city of Ancona, information security and cybersecurity play a fundamental role, especially thanks to the contribution of D..
0
4036
Network security is a key priority for businesses and individuals who want to protect their data and infrastructure. There are numerous network vulner..
0
19376
Network-Attached Storage (NAS) is a storage device connected to a local area network or the Internet. It is designed to both keep data securely and al..